
Categories
Money money money...
Could we help you? Please click the banners. We are young and desperately need the money



kSnip custom FTP upload script - Upload screenshots to your FTP server fully automatic



Mastering kSnip FTP Uploads: An Essential Script for Your Workflow
If you've ever been in the midst of a productive workflow and found yourself wishing for a smoother way to upload your kSnip screenshots to FTP, you're not alone. With the rise of remote work and the ever-growing need for quick and secure file sharing, an efficient process is more important than ever. Today, I'm thrilled to share a powerful script that seamlessly integrates kSnip with FTP uploads, streamlining your screenshot-sharing process.
The Challenge: kSnip and FTP
Out of the box, kSnip is a fantastic tool for capturing and annotating screenshots. But when it comes to uploading these captures to FTP servers, especially with SSL protection, things aren’t as straightforward. Some users might opt for manual uploads, while others could be juggling between multiple tools. Enter our solution: the kSnip FTP Upload script.
How Does the kSnip FTP Upload Script Work?
The beauty of this script lies in its simplicity. By using lftp, a commendable command-line utility supporting various protocols including FTP with SSL, the script effortlessly uploads your screenshots to your FTP server. And not just that, it renames the file using a timestamp format to ensure unique and traceable filenames, making your organization process a breeze.
#!/bin/bash
# Wait 1 seconds for the screenshot file to be written to the harddrive
sleep 1
# If you are running kSnip as a Flatpak app you need to copy the lftp binary from /usr/bin/lftp to your users' path.
# Because flatpak is blacklisting the /usr path and you cannot run any binary from there
LFTP_PATH="/home/user/scripts/lftp"
# Configuration variables
FTP_SERVER_URI="ftp.server.url"
FTP_USERNAME="ftp_username"
FTP_PASSWORD="ftp_password"
# The URL to the webserver where the image will be accessible after uploading. Enter the URL without a tailing "/" and also without any image name.
URL_PATH="https://your-webserver-url"
# Set current date/time in order to create a proper filename on the remote server
CURRENT_TIMESTAMP=$(date +"%Y-%m-%d-%H%M%S")
# Get the file extension of the kSnip temp file
FILE_EXTENSION="${1##*.}"
# Build the new remote filename
REMOTE_FILENAME="${CURRENT_TIMESTAMP}.${FILE_EXTENSION}"
# Build the full URL path to the image on the remote server
IMAGE_URL_PATH="${URL_PATH}/${REMOTE_FILENAME}"
# Use lftp for TLS/SSL FTP support (you might need to install this utility)
LFTP_OUTPUT=$(${LFTP_PATH} -e "set ftp:ssl-protect-data true; set ssl:verify-certificate no; put ${1} -o /${REMOTE_FILENAME}; bye" -u ${FTP_USERNAME},${FTP_PASSWORD} -p 21 ftp://${FTP_SERVER_URI} 2>&1)
# Check the result of the FTP upload
if [ $? -eq 0 ]; then
# Copy the IMAGE_URL_PATH to clipboard by simply returning it to kSnip, which simply copies the return value of the script into the clipboard
echo "${IMAGE_URL_PATH}"
# Send a nice desktop notification
notify-send "Screenshot successfully uploaded to ${IMAGE_URL_PATH}"
else
# Notify user of the failure
notify-send "Error uploading screenshot. Error: ${LFTP_OUTPUT}"
fiAdd the script to kSnip
Add the script like this in the kSnip configuration and don't forget to set the Uploader type to "script" in the "Uploader" settings menu:
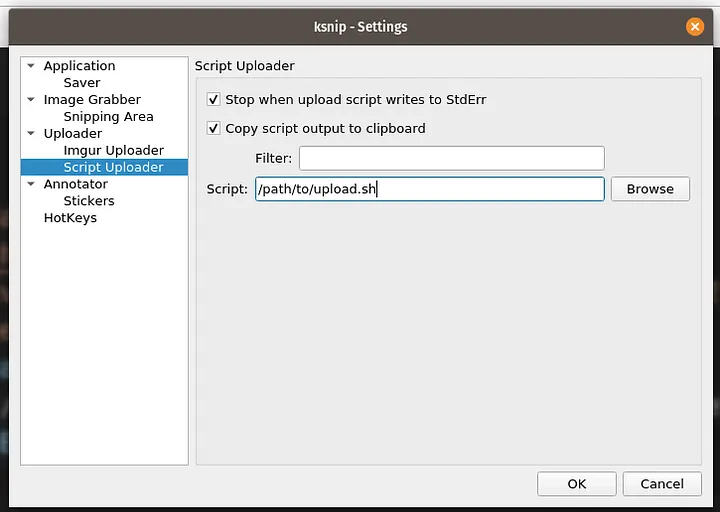
Why Use the kSnip FTP Upload Script?
Automation and Efficiency: No more tedious manual uploads. With this script, you're one step closer to an automated workflow.
Unique Filenames: Say goodbye to confusion. With timestamp-based filenames, every screenshot is distinct and easy to trace.
Security: With SSL protection, your screenshots are uploaded securely, ensuring peace of mind.
Getting Started
Before diving in, ensure you have lftp installed and available. For those using kSnip as a Flatpak app, a quick tip: you might need to copy the lftp binary from /usr/bin/lftp to your user's path, as Flatpak blacklists the /usr path. Once you've set up your environment, input your FTP details into the script, and you're ready to roll!
Final Thoughts
The kSnip FTP Upload script bridges the gap between screenshot capture and secure file sharing. Whether you're collaborating with a team, sharing a bug report, or just organizing your screenshots, this script is an invaluable addition to your toolkit.
Got any thoughts or improvements? We'd love to hear them in the comments below!
